Hackers are merely a Google search away from hacking your network.
By Brandon Barney, CISSP
Devices, like routers, come straight from the vendor with factory settings like default usernames and passwords. Defaults make device installation and support easier, but also mean every model originates with the same username and password. When those defaults aren’t changed, you give hackers Wonka’s Golden Ticket into your system.Watch the video to learn more about vendor supplied defaults.
Want to see more vids like this? Subscribe on YouTube formore security tips.
During a recent SecurityMetrics forensic investigation, we discovered the IT company that configured the compromised merchant also set up 50 additional merchants with the same configuration and passwords. Yikes.
Once the hacker cracked the username/password, it was all downhill from there.
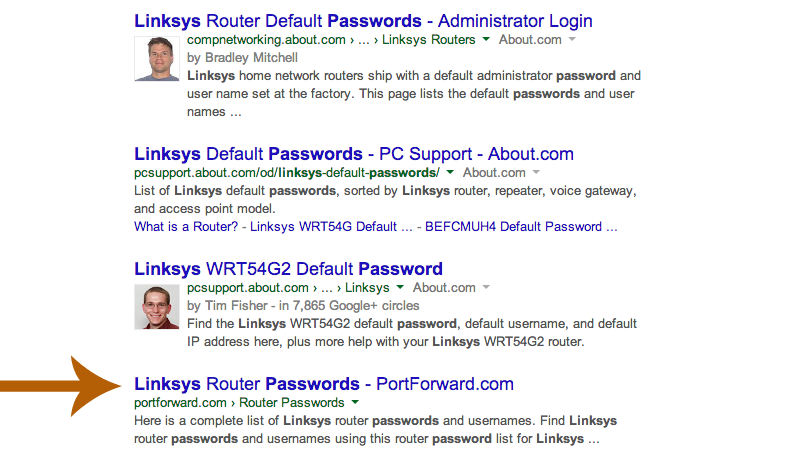
Don’t believe it? Google your device. Type: “[manufacturer] [model] default password.” It’s really quite simple to find your device’s default settings, along with a slew of hackalicious goodies.
 |
| This link here looks promising... |
 |
| Looks like no matter what model Linksys router, the default username and password are usually admin. Doh! |
Still don’t believe me? Here’s a sampler of a few common usernames/passwords.
- Username: admin, username, test, admin1, sysadmin, default, public
- Password: password, admin, 000000, 123456, test, 1, changeme, letmein
Have a business security question? Tweet me and you may see your question answered on the next SecurityQ.
Brandon Barney, CISSP, is the Security Support Director at SecurityMetrics and has over 10 years of compliance, data security, and database management experience.