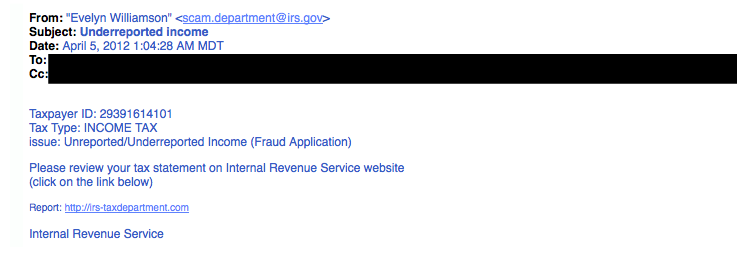
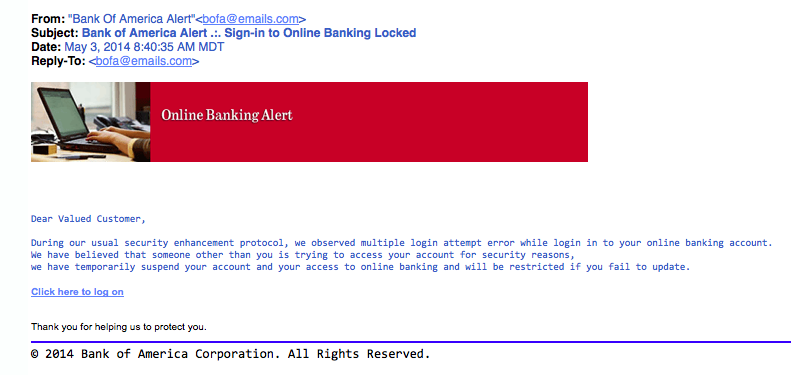
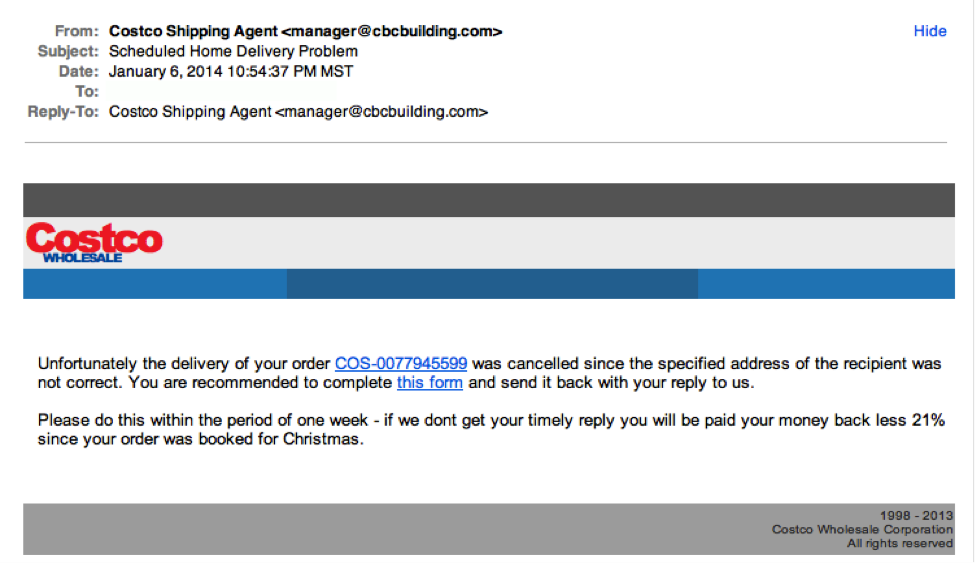
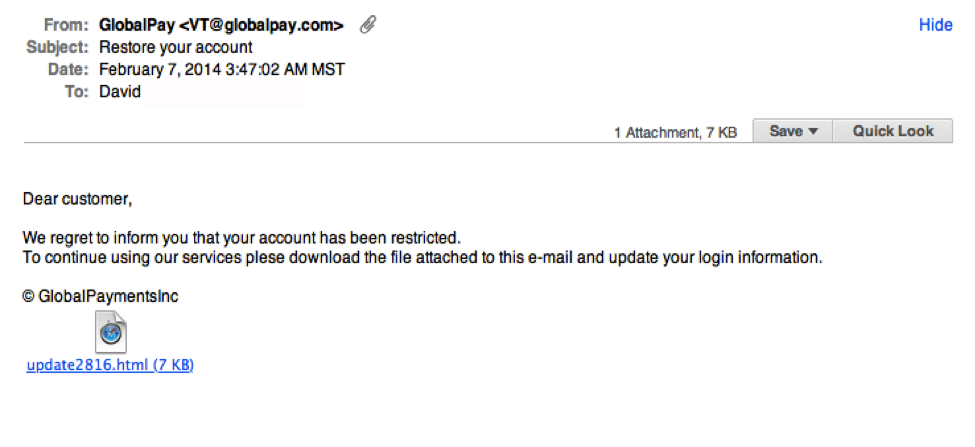
In recent security conferences, network printers have been revealed to be potential doorways into a secure network. How can this be? They just receive print jobs from inside your network and create hard copies...right? Nowadays, multifunction printer devices have many avenues for receiving and sending communication and may inadvertently be storing sensitive information about your network. Here are some things you should know about your potential “informant.”
I need to secure a printer?!Often printer security is neglected or ignored. ”It’s just a printer. Why do I need to secure it?” Commonly, printers are plugged into the corporate network, integrated with business systems, and given Local Area Network (LAN) authentication. New passwords aren’t generated to replace factory defaults and neither are passwords for administrative function access. Since they are considered hardware, printers are bypassed on the regular system update/patch management schedule. Unsecure setup of these devices can lead to serious exposure of sensitive data.
Dangerous printer capabilities
Many of these features, if not secured, could result in sensitive data or password harvesting.
- Document scanning to a file. The printer allows access to a scanned file via File Transfer Protocol (FTP) or may copy the file to a network file server. Authentication credentials to that file server are stored by the printer.
- Document scanning to email. Credentials are required to access the local mail server. A local printer may also store email and user addresses.
- Email notification. An address book of internal e-mails may be stored by the printer to enable various types of notification (fax, print job finished, etc.). If this information can be gleaned from the printer, the attacker now knows more than he should about internal e-mails.
- A remote administration portal, usually an embedded web server, can be reached from the network where the printer resides or even from the Internet. Often system administrators are not changing the default access password to this administration page.
How are printers being attacked?
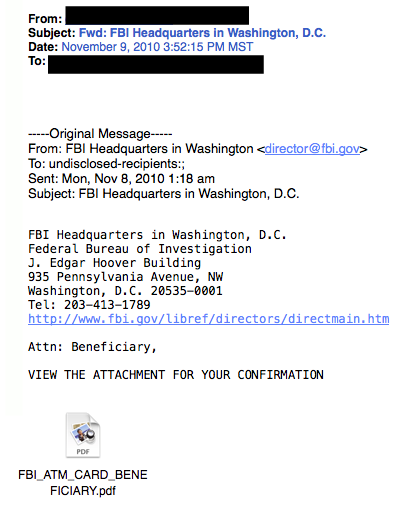
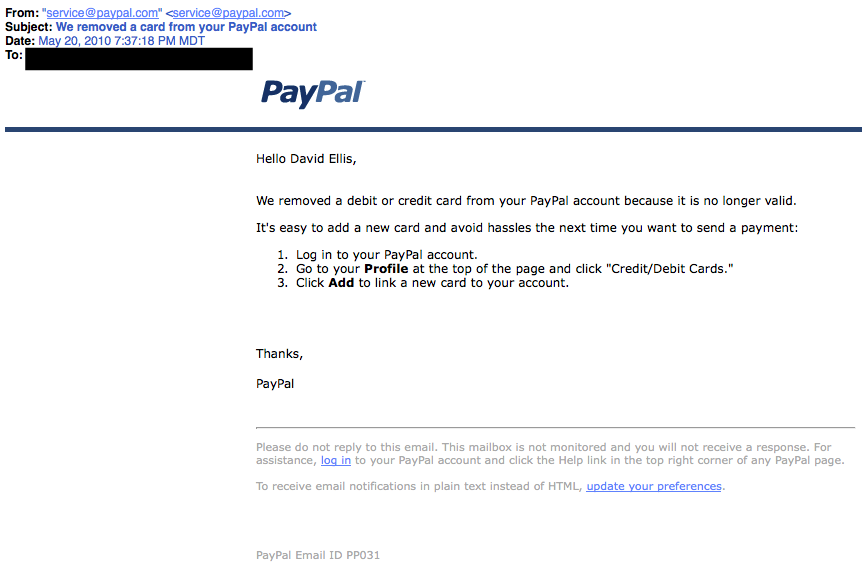
One of the most common and simple attacks hackers use on these devices is leveraging the default password set by the manufacturer to gain access to the administrative portal on the printer. Even if defaults have been changed, a simple attack against this administrative portal may allow someone to bypass the authentication layer of the device. (There are known attacks of this sort on some HP and Toshiba devices using a well-placed extra character in the administrative portal’s URL.) With access to the portal, it can be very easy to glean network access information.
IT personnel often use directory service administrator level username/passwords when setting up the printer to access shared resources. This login information might be visible from the printer’s administrative interface or accessible directly from the printer’s password settings page by viewing hidden HTML variables kept right in the page HTML source. Not securely protecting password information allows the hacker to collect this information from the printer and then “become” an administrator of the network or other sensitive systems.
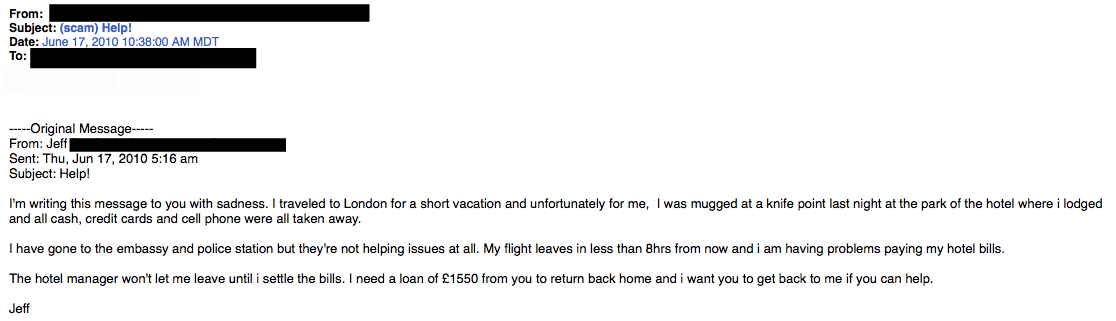
Some printer attacks allow an attacker to enumerate all email addresses stored in the address book and maybe even file share credentials that allow the printer to deposit scanned files direct to specific file servers. This data would then allow the attacker to gain authenticated access to many systems within the network environment, and from there direct his attacks to systems where financial or other sensitive company information may be stored or processed.
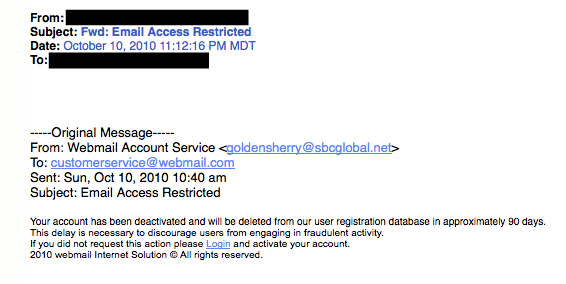
Other types of attacks trick the printer into communicating with an attacker rather than a standard configured service like Lightweight Directory Access Protocol (LDAP) and Simple Mail Transfer protocol (SMTP). The results of these types of attacks can allow an attacker to gather internal IP addresses, communication port information, and usernames/passwords.
What can I do?- Change default passwords on printers.
- Develop an update management process to keep printer software and firmware up–to-date.
- Avoid using administrator level usernames and passwords when granting the printer access to network resources.
- Tools like Praeda are used by security professionals to help secure printers. (Note: these same tools are also available to attackers). You can follow Praeda’s progress at www.foofus.net
Multifunction and network enabled printers may contain very sensitive information about your internal network and may be a “weak link” in your overall security strategy. Do not neglect them.
--The SecurityMetrics Audit Team